DNS Cache Snooping
December 12, 2022
By Gavin Debetaz, Information Security Analyst
In the present day and age, most employees know that they should not use their company internet for non-business purposes. Most organizations require their employees to read and sign an Acceptable Use Agreement to ensure that they understand what websites can and cannot be accessed. They will also use firewalls and other software solutions to monitor and control what websites employees are accessing. Blocking known malicious sites provides a great preventative measure for a variety of cybersecurity incidents, such as data exfiltration or introduction of malware to systems. Even with these filters and monitoring in place, there is another avenue that attackers can use to fool your employees. If an organization does not have their network configurations set properly, an outside attacker can snoop and discover the domains of all the websites that employees of the organization have visited. With this information, an attacker could use this information to spoof trusted sites that your employees use every day. In this article, we will break down how this attack works, the possible consequences, and how to prevent it.
This attack targets an organization’s DNS server, which operates on port 53 using TCP and UDP. DNS servers are crucial for business functions because they allow users to search websites without knowing their exact IP address. Chances are most employees don’t know the IP address for the websites they frequent such as Google (8.8.8.8 by the way), so they use a DNS server to access these sites. Simply put, when an employee enters a website domain into their search bar, such as “www.website.com”, a DNS query is formed by the DNS server behind the scenes, which resolves it into it’s appropriate IP address. The DNS server takes these queries and caches them into a temporary storage location. By caching the data, the DNS server can operate more efficiently, because when that same website is accessed, the DNS server does not have to make a full lookup. Instead, it references to the cache and accesses the IP address much more quickly, reducing bandwidth and CPU consumption. However, if a DNS server is not configured properly, this cache becomes accessible, and therefore very troublesome for an organization. When an malicious attacker leverages this information, we call it a DNS cache snooping attack.
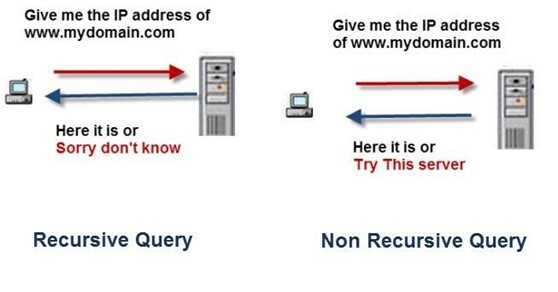
The way a DNS cache snooping attack works is when an attacker queries their target DNS server to check if it has a specific DNS record cached. This can be done by running scripts using various networking tools, such as NMAP. With this, they can discover if the users in a target network have recently visited that website. Attackers will typically use a large list of domains, ranging from vendors, service providers, and common websites to discover what websites the users frequent. This attack occurs when DNS servers allow name recursion, which is a necessary function for many DNS servers. DNS servers use recursion to resolve DNS names from zones that are not held locally, such as the internet. So, without this function, the organization may have normal business functions disrupted.
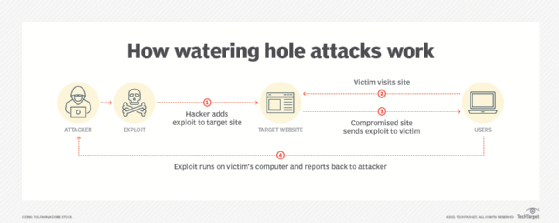
There are several possible consequences to this attack, most of them involving social engineering tactics. If an attacker has access to an organization’s recent searches, they can use that knowledge to target the employees using social engineering attacks, such as phishing emails. For example, an attacker may discover that an organization uses a certain company as their ISP. An attacker who discovers this could craft an email from their ISP, and tailor it specifically to the organization. This would prove to be more effective than a random email. In addition to this, an attacker will understand the web-surfing patterns of the organization. With knowledge of this, an attacker could set up a watering hole attack to lure users of the organization. Once an employee clicks on the watering hole site, malware can be uploaded to their device which can easily be devastating for an organization. Finally, an attacker could discover what external email servers an organization uses. With knowledge of this, the attacker will be better prepared to target the organization’s email servers.
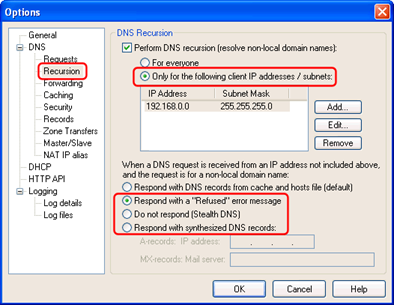
All the solutions to this vulnerability involve configuration changes. The simplest fix to this vulnerability is to not have the organization’s DNS servers be externally accessible. Typically, most organizations do not have a need for their DNS servers to be externally facing. The main instance is if an organization has publicly accessible IP addresses in their internal network that they want the public to be able to access. For this to work, the organization must have their DNS server externally facing, but it is best practice to put externally facing ports such as this in a DMZ. The second solution is to not allow public access to the DNS servers on the organization’s networks that require recursion to function properly. This solution works well, but requires multiple DNS servers with unique configurations. Finally, the organization can disable recursion on their DNS Servers, but as previously mentioned this could cause issues for the organization’s business functions and should be investigated beforehand. Also, some vendors may own the server and not allow an organization to change their configuration settings. In this case, the organization should contact their vendor to make the change if they are susceptible to the attack.
TraceSecurity recommends performing penetration tests and vulnerability assessments on your networks regularly to check for vulnerabilities such as these. Organizations could be vulnerable to this type of attack, and would never know unless they conduct testing or until it is too late. Anyone can be susceptible to these types of attacks, and it is important to perform regular testing to ensure your organization is protected.